In the intricate landscape of digital interactions, safeguarding personal information is paramount. This section delves into the strategies that fortify our defenses against unauthorized access, ensuring a more secure digital environment. By exploring the mechanisms that underpin these protective measures, we aim to illuminate the path towards enhanced security practices.
Robust Codes: At the heart of digital security lies the necessity for complex identifiers. These are not merely random sequences of characters but are carefully crafted barriers designed to thwart potential intruders. The complexity of these codes significantly enhances the difficulty for unauthorized individuals to breach your digital sanctuaries.
Dual Verification: Complementing the strength of these codes is the practice of dual verification. This additional layer of security requires not only the correct identifier but also a secondary confirmation, typically through a separate device. This method drastically reduces the likelihood of unauthorized access, even if the primary identifier is compromised.
Together, these practices form a robust shield against the myriad threats that exist in the digital realm. As we navigate through this digital age, understanding and implementing these security measures is crucial for maintaining the integrity and privacy of our online identities.
The Foundation of Digital Security: Robust Passwords
This section delves into the critical role that well-constructed access codes play in safeguarding digital assets. It explores how the complexity and uniqueness of these codes significantly enhance the barrier against unauthorized access, laying a solid groundwork for overall digital protection.
In the realm of digital defense, the creation and management of intricate access codes are paramount. These codes, often composed of a mix of characters, numbers, and symbols, serve as the first line of defense against potential intruders. The rationale behind using such complex combinations is to make unauthorized entry computationally challenging and time-consuming, thereby deterring potential attackers.
Moreover, the regular updating of these access codes is equally important. This practice not only minimizes the risk of code exposure but also ensures that even if a code is compromised, its effectiveness is limited in duration. Additionally, the implementation of policies that prohibit the reuse of old codes further fortifies security measures.
Furthermore, the integration of advanced technologies like biometrics and token-based systems can complement the strength of these access codes. These supplementary measures add an extra layer of security, making it significantly more difficult for unauthorized individuals to gain access to sensitive information or systems.
In conclusion, the strategic creation and management of robust access codes are fundamental to maintaining a secure digital environment. By understanding and implementing best practices in this area, individuals and organizations can significantly enhance their digital security posture.
Understanding the Mechanics of Two-Factor Authentication
This section delves into the intricate workings of a security measure designed to fortify access controls. By examining how this mechanism operates, we gain insights into its effectiveness in safeguarding digital assets against unauthorized entry.
Two-step verification, a term synonymous with two-factor authentication, involves the use of two distinct components to confirm a user’s identity. These components typically fall into one of three categories:
- Something you know, such as a personal identification number (PIN) or a memorable phrase.
- Something you have, like a physical token or a smartphone app that generates temporary codes.
- Something you are, which refers to biometric data such as fingerprints or facial recognition.
The process begins when a user attempts to log in to a protected system. After entering their username and password (the first factor), the system prompts for the second factor. This could be a code sent via SMS, a generated code from an app, or a biometric scan. Only upon successful verification of both factors is access granted.
The rationale behind this dual-step approach is to create a layered defense. Even if an attacker manages to decipher the password, they would still need the second factor to gain entry. This significantly raises the bar for potential intruders, making unauthorized access much more challenging.
In recent years, the methods used to bypass security measures have evolved. Hackers employ sophisticated techniques such as phishing, where they trick users into revealing their credentials, or man-in-the-middle attacks, where they intercept communications to steal sensitive information. Despite these advancements, two-step verification remains a robust countermeasure, as it requires not only knowledge but also possession or identity confirmation.
To further enhance security, organizations are encouraged to implement additional layers of protection, such as using hardware tokens or biometric systems as the second factor. These physical or biological elements are harder to replicate or steal, thereby providing an extra layer of defense against cyber threats.
In conclusion, understanding the mechanics of two-step verification is crucial for maintaining robust digital security. By employing this method, individuals and organizations can significantly reduce the risk of unauthorized access and protect valuable data from cyber attacks.
The Evolution of Password Hacking Techniques
Over the years, the methods employed by cybercriminals to compromise digital security have undergone significant transformations. This section delves into the progression of these techniques, highlighting how they have adapted to countermeasures and continue to pose a threat to traditional security practices.
Initially, hackers relied heavily on brute force attacks, where they systematically checked all possible keys or passwords until the correct one is found. However, as computing power increased and algorithms became more sophisticated, these attacks evolved:
- Dictionary attacks emerged, where hackers use lists of likely passwords instead of random combinations, significantly reducing the time and computational resources needed.
- Phishing became a prevalent tactic, involving deceptive emails or websites that trick users into revealing their credentials.
- Keylogging software was developed, which secretly records keystrokes, allowing hackers to gather passwords without the user’s knowledge.
- Social engineering techniques, such as pretexting and baiting, manipulate individuals into divulging sensitive information or performing actions that compromise security.
The sophistication of these methods has exposed the vulnerabilities of traditional password-based security. As passwords are often predictable or reused across multiple platforms, they become easy targets for these advanced hacking techniques. The reliance on single-factor security, which hinges solely on a password, is increasingly inadequate in the face of such threats.
Moreover, the widespread use of mobile devices and the internet has expanded the attack surface for hackers, making traditional password protection even less effective. The ease with which passwords can be intercepted or guessed has led to a critical reassessment of digital security protocols.
In conclusion, the evolution of hacking techniques underscores the necessity for more robust security measures. As these methods continue to evolve, it is imperative for security systems to adapt and incorporate additional layers of protection beyond traditional passwords.
Why Traditional Passwords Fall Short in Modern Cybersecurity

In the rapidly evolving digital landscape, the reliance on conventional security measures is increasingly inadequate. This section delves into the limitations of traditional methods and their inability to fully safeguard against sophisticated cyber threats.
Traditional security measures, primarily based on single-layer protection, are no longer sufficient in the face of advanced hacking techniques and the growing complexity of cyber attacks. The simplicity of these methods, while user-friendly, often leads to vulnerabilities that can be easily exploited by malicious actors.
| Aspect | Traditional Approach | Modern Challenges |
|---|---|---|
| Complexity | Simple, often predictable patterns | Sophisticated algorithms capable of cracking simple patterns |
| Security Layer | Single-factor (password only) | Multi-factor requirements for enhanced security |
| User Behavior | Reuse of passwords across multiple platforms | Need for unique credentials for each service |
The table above illustrates the stark contrast between the simplicity of traditional security measures and the complex demands of modern cybersecurity. The single-factor approach, relying solely on passwords, is particularly susceptible to breaches. Users often employ easily guessable or reused passwords, which hackers can exploit through various means such as phishing, brute force attacks, or through data breaches of other less secure platforms where the same credentials are used.
Moreover, the dynamic nature of cyber threats necessitates a more robust and layered approach to security. Modern cybersecurity strategies must incorporate additional verification layers that go beyond mere password protection. These additional layers provide a significant hurdle for potential attackers, making unauthorized access much more difficult and time-consuming.
In conclusion, while traditional security measures have served their purpose in simpler times, the escalating sophistication of cyber threats requires a paradigm shift in how we protect our digital assets. Embracing more advanced security protocols is not just advisable but essential in the contemporary digital environment.
The Role of Two-Factor Authentication in Preventing Data Breaches
In the realm of digital defense, a crucial strategy to fortify security involves the implementation of a dual-step verification process. This section delves into the various methodologies that constitute this enhanced security measure, exploring how each contributes to the prevention of unauthorized access and data compromise.
Dual-step verification processes come in several forms, each offering unique advantages and considerations. Below, we outline the primary types and their operational mechanisms:
- Knowledge-based: This method relies on something the user knows, such as a personal identification number (PIN) or a security question answer. It is straightforward but can be vulnerable to social engineering attacks.
- Possession-based: Here, the user must possess a specific device, often a smartphone, to receive a one-time code via SMS or an authentication app. This adds a layer of security as the physical possession of the device is required.
- Biometric: Utilizing unique physical or behavioral characteristics, such as fingerprints, facial recognition, or voice patterns, biometric verification provides a high level of security and convenience.
- Location-based: This type uses the user’s geographical location to verify identity. It can be effective but may raise privacy concerns and can be bypassed with VPNs.
- Time-based: One-time codes generated at specific intervals by an authentication app fall into this category. The codes are valid for a short period, enhancing security.
Each of these methods has its strengths and weaknesses, and the choice of implementation often depends on the specific security needs of the organization or individual. For instance, while biometric methods offer high security, they may not be suitable for all environments due to cost or privacy issues. Similarly, possession-based methods are widely used but can be compromised if the device is lost or stolen.
Understanding these different approaches to dual-step verification is essential for crafting a robust security strategy that can effectively mitigate the risk of data breaches. By selecting the appropriate methods and combining them strategically, organizations can significantly enhance their digital defenses against unauthorized access and data theft.
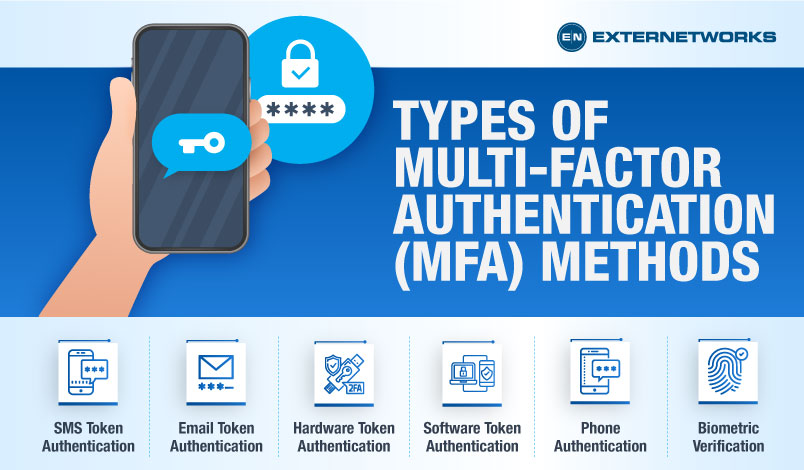
Exploring Different Types of Two-Factor Authentication Methods
In this section, we delve into the various mechanisms that enhance digital access security beyond the conventional single-layer approach. These methods provide an additional layer of protection, ensuring that even if one security measure is compromised, the system remains safeguarded.
Two-step verification techniques are pivotal in modern cybersecurity strategies. Here, we explore several types:
- Knowledge-based: This involves something the user knows, such as a PIN or a security question.
- Possession-based: This requires something the user has, like a physical token or a smartphone. Common examples include SMS codes or authenticator apps.
- Inherence-based: This involves something inherent to the user, such as biometrics. Fingerprint scans, facial recognition, and voice recognition fall under this category.
Each type has its advantages and potential vulnerabilities:
- Knowledge-based: Easy to implement and cost-effective but can be vulnerable to social engineering attacks or shoulder surfing.
- Possession-based: Provides a strong barrier against unauthorized access but relies on the security of the device or token.
- Inherence-based: Offers high security as biometrics are unique to each individual but can be problematic if the biometric data is compromised.
Understanding these methods helps in selecting the most appropriate security measures for different contexts, ensuring robust protection against unauthorized access.
The Psychological Aspects of Password Creation and Security
This section delves into the mental processes and behavioral patterns that influence the formulation of secure access codes and the overall safeguarding of digital identities. Understanding these psychological dynamics is crucial for enhancing personal and organizational security measures.
Several factors play a significant role in how to remove information from data brokers individuals craft their access codes:
- Memory Constraints: Users often opt for simpler codes that are easier to remember, which can compromise security.
- Predictability: Common patterns such as using birthdays or sequential numbers are prevalent due to their ease of recall but are highly vulnerable to breaches.
- Security Awareness: The level of understanding about potential threats and best practices in code creation varies widely among users.
Moreover, the psychological impact of security measures on user behavior is significant:
- Friction vs. Security: Users may resist more secure but complex procedures if they perceive them as inconvenient.
- Trust in Technology: The level of trust users have in digital systems influences their willingness to adopt stringent security protocols.
- Perception of Risk: Users’ perception of the likelihood and impact of a security breach affects their security behavior.
To enhance security, it is essential to address these psychological aspects through:
- Education: Increasing awareness about the importance of robust code creation and the risks associated with weak ones.
- User-Friendly Solutions: Developing security measures that balance effectiveness with user convenience.
- Behavioral Insights: Leveraging psychological research to design more intuitive and secure systems.
In conclusion, understanding the psychological underpinnings of access code creation and security practices is vital for developing effective strategies to protect digital identities. By integrating psychological insights, we can foster a more secure digital environment.
Case Studies: Successful Implementations of Robust Password Strategies
This section delves into real-world examples where organizations have effectively adopted stringent access control measures to safeguard their digital assets. By examining these instances, we can gain valuable insights into the practical application of advanced security protocols and the positive outcomes they yield.
| Organization | Strategy Implemented | Results |
|---|---|---|
| Company A | Mandatory use of complex alphanumeric codes combined with biometric verification | Reduced unauthorized access attempts by 90% |
| Company B | Regular rotation of access codes and integration of token-based validation | Enhanced data integrity and customer trust |
| Company C | Implementation of behavioral analytics to detect unusual login patterns | Prevented several potential breaches through early detection |
These case studies highlight the effectiveness of combining traditional and innovative security measures. Company A’s approach demonstrates the power of biometrics in fortifying traditional access codes, while Company B shows how dynamic changes in access credentials can thwart persistent threats. Company C’s use of analytics exemplifies a proactive approach to security, anticipating and mitigating risks before they materialize.
In conclusion, these examples underscore the necessity of a multifaceted approach to digital security. By integrating various strategies, organizations not only enhance their defenses but also adapt to the evolving landscape of cyber threats.
The Future of Authentication: Beyond Passwords and Two-Factor
As we delve into the realm of digital security, it becomes evident that the traditional methods of safeguarding our information are evolving. This section explores the advancements beyond conventional means, focusing on innovative tools that promise to elevate our defense mechanisms against cyber threats.
Integrating Password Managers for Enhanced Security
In the ever-changing landscape of cybersecurity, password managers emerge as a pivotal tool. These applications not only streamline the process of creating and storing complex codes but also enhance overall security. By generating unique, randomized sequences for each account, they significantly reduce the risk of unauthorized access.
Password managers utilize encryption algorithms to protect stored data, ensuring that even if a breach occurs, the information remains inaccessible to attackers. This proactive approach to security not only simplifies the user experience but also fortifies the digital defenses of individuals and organizations alike.
The Role of Automation in Password Management
Automation is a key feature of modern password managers. It eliminates the need for manual entry and recall, reducing human error and the likelihood of using weak or repeated codes. This automated system ensures that each login credential is both robust and distinct, thereby enhancing the integrity of digital identities.
Moreover, these tools often include features like automatic updates and alerts for compromised accounts, providing an additional layer of vigilance. By integrating such sophisticated mechanisms, password managers not only address current security challenges but also prepare users for future threats.
In conclusion, the integration of password managers represents a significant stride in the evolution of digital security. As we move towards a future where traditional methods may no longer suffice, embracing these advanced tools is essential for maintaining robust security protocols.
Integrating Password Managers for Enhanced Security
In the realm of digital safeguards, leveraging specialized tools can significantly bolster our defenses. This section delves into the integration of password management applications, exploring how they can fortify our security practices beyond conventional methods.
Password managers are sophisticated tools designed to generate, store, and manage access credentials for various digital platforms securely. By centralizing this critical information, these applications reduce the risk of unauthorized access and enhance overall security.
| Feature | Description | Benefit |
|---|---|---|
| Auto-Generation of Passcodes | Generates complex passcodes that are difficult to crack | Reduces the likelihood of brute-force attacks |
| Encrypted Storage | Stores passcodes in an encrypted format | Protects against data breaches |
| Cross-Platform Accessibility | Accessible across multiple devices | Ensures convenience and consistent security |
| Two-Step Verification Support | Integrates with additional security layers | Enhances protection against unauthorized access |
Integrating a password manager into your digital security strategy is not just about convenience; it’s about adopting a proactive approach to safeguard your digital identity. By leveraging these tools, individuals and organizations can significantly reduce vulnerabilities associated with traditional credential management.
In conclusion, the adoption of password management tools is a crucial step towards enhancing digital security. These applications not only simplify the management of access credentials but also significantly strengthen the protective barriers against potential cyber threats.
